Explore key tools, smart features, and expert insights...
Enterprise users interact with external domains every day. While many domains are legitimate, unsecured or non-compliant access introduces measurable risk.
Unsecured browser behavior can expose organizations to malware delivery, data interception, credential harvesting, and regulatory concerns. In remote and hybrid environments, where users operate beyond traditional network boundaries, this exposure becomes more pronounced.
Chrome Enterprise Premium enables organizations to apply consistent governance to browser access patterns. Instead of treating the browser as a passive channel, it becomes an enforceable security layer.
Relying only on network-layer controls is no longer sufficient in a SaaS-driven, browser-centric workplace. Chrome Enterprise Premium strengthens enforcement directly at the browser layer, where user interaction occurs.
It supports the following capabilities:
Administrators can define browser usage policies aligned with enterprise security standards. Access parameters can reflect organizational risk tolerance and compliance requirements.
Consistent browser settings reduce fragmented security posture across devices, departments, and geographic regions. Governance becomes standardized rather than discretionary.
By enforcing structured browsing policies, organizations reduce exposure to preventable domain-level threats. Risk is managed proactively rather than after an incident.
Centralized browser governance enables clearer visibility into policy compliance and configuration status at scale. Leadership gains insight into posture rather than relying on assumptions.
This approach shifts browser management from reactive troubleshooting toward structured oversight.
Before enforcing new controls, IT and security teams need a clear understanding of existing behavior.
Common questions include:
How frequently are unsecured domains accessed?
Which devices show elevated exposure?
Is unsecured browsing concentrated within specific user groups?
How does this behavior influence overall security posture?
Without baseline visibility, enforcement may be misaligned with actual exposure patterns. Data-driven governance begins with measurement.
The Chrome Readiness Tool provides insight into unsecured domain access incidents across installed devices.
Its dashboard highlights:
Domains accessed that fall outside the defined security standards
Distribution of unsecured browsing behavior across the organization
This data helps leaders quantify exposure before formalizing new policies, swapping broad restrictions for targeted governance. While the Chrome Readiness Tool doesn't enforce rules, it identifies the high-impact areas where enforcement will reduce the most risk.
Chrome Enterprise Premium provides structured browser controls. The Chrome Readiness Tool provides the insight that informs those controls.
In a browser-centric workplace, domain-level risk cannot be treated as peripheral. It must be governed with the same rigor applied to endpoints and identity systems.
By combining the enforcement capabilities of Chrome Enterprise Premium with the visibility delivered by the Chrome Readiness Tool, organizations strengthen resilience, improve compliance alignment, and reduce preventable exposure across their digital environment.
Browser extensions can improve productivity. They can also introduce measurable risk. Many extensions request broad permissions, interact directly with web content, and access enterprise data within active sessions.
In distributed work environments, unmanaged extensions accumulate quietly. Different teams install different tools. Configurations drift. Over time, this expands the attack surface and weakens standardization across the organization.
Chrome Enterprise Premium enables organizations to shift from reactive extension cleanup to structured extension governance at the browser level.
Instead of allowing extension sprawl, Chrome Enterprise Premium provides centralized administrative oversight with enforceable policy controls.
Key advantages include:
Administrators can define which extensions are allowed, restricted, or blocked across the organization. Controls are applied consistently, reducing reliance on manual review.
Approved extensions can be deployed in a controlled manner. This limits shadow IT behavior and removes inconsistent installations between departments.
Centralized policies maintain a consistent browser posture across devices and user groups. This reduces unpredictable security gaps caused by unmanaged installs.
Structured extension controls support internal compliance frameworks and enterprise security standards. Browser configuration becomes auditable and aligned with policy.
This model does not eliminate extensions. It brings them into a governed ecosystem with defined guardrails.
Before implementing enforcement, organizations often need a clear inventory of what already exists across their environment.
Security and IT teams typically ask:
How many extensions are currently installed?
Which extensions are unverified or unmanaged?
Where are high-risk extensions concentrated?
How does extension usage correlate with device security posture?
Without centralized reporting, answering these questions requires manual effort and fragmented tooling. That creates blind spots.
Visibility becomes the foundation for structured governance.
The Chrome Readiness Tool provides insight into unverified extensions installed across devices within the organization.
Its dashboard surfaces:
Extension footprint across the enterprise
Display unverified extensions
Device-level distribution of exposure for extensions
This enables IT leaders to move from assumptions to measurable data. Instead of reacting after an incident, teams can evaluate extension-related exposure in advance and prioritize areas of concern.
The Chrome Readiness Tool does not replace enforcement. It clarifies where enforcement will have the greatest impact.
The relationship between Chrome Enterprise Premium and the Chrome Readiness Tool is sequential and strategic. Together, they support a structured extension governance.
As browser usage continues to expand, extension management must evolve from informal oversight to centralized governance. Unverified extensions are not simply productivity tools. They represent executable code operating inside trusted sessions.
By combining visibility with enforceable controls, organizations reduce unnecessary exposure while preserving user productivity and operational consistency.

In today’s enterprise environment, the browser is the primary access point to business-critical applications. Finance systems, SaaS platforms, internal dashboards, and collaboration tools all run inside authenticated browser sessions that provide direct access to sensitive data.
That session is not just a technical layer. It represents active trust.
As hybrid work expands and SaaS adoption increases, protecting the browser session becomes a strategic priority. Traditional security models emphasize identity verification at login. However, once authentication is complete, the live session itself becomes a high-value target.
Chrome Enterprise Premium strengthens security at the point where work actually happens, inside the browser. It introduces centralized policy enforcement, contextual access controls, and structured governance across user sessions. Instead of relying only on identity-layer protections, organizations can secure the environment where authenticated activity operates.
Session theft occurs when attackers hijack an authenticated browser session, bypassing login controls without needing credentials. In many cases, identity systems do not detect this because authentication technically already succeeded.
Chrome Enterprise Premium complements identity and endpoint protections by adding structured browser-level controls.
Administrators can apply policies based on device posture, user context, and organizational standards. This reduces the risk of unauthorized session reuse and limits exposure when a device falls outside compliance thresholds.
Security teams can enforce consistent browser configurations across distributed environments. This minimizes policy drift and removes inconsistencies that create exploitable gaps.
Browser-level controls aligned with enterprise policy reduce exposure during active sessions, especially when users interact with sensitive SaaS applications. Access decisions reflect context, not just credentials.
The browser shifts from being a passive conduit to a governed security surface. Configurations are standardized. Controls are enforced. Risk is systematically reduced.
This approach moves session protection from reactive monitoring toward structured prevention.
Enforcement is critical, yet many organizations lack clear insight into where session-related risks are emerging across their environment.
Before strengthening policy controls, IT and security teams often need clarity:
Where are session risks concentrated?
How many devices show elevated exposure?
Are certain domains or user groups more vulnerable?
What is the distribution between secure and unsecured devices?
Without visibility, enforcement becomes assumption-driven. Visibility turns risk into measurable data.
The Chrome Readiness Tool provides a consolidated view of browser-related risks, including session theft indicators across installed devices.
Within its web dashboard, teams can identify:
Devices potentially exposed to session-related threats
Organization-wide risk metrics tied to browser usage
This visibility does not replace enforcement. It strengthens decision-making.
For many enterprises, the Chrome Readiness Tool becomes the analytical starting point. It quantifies exposure and highlights configuration gaps that may not be visible through traditional endpoint reporting.
Chrome Enterprise Premium and the Chrome Readiness Tool serve complementary roles in a modern browser security strategy.
Chrome Enterprise Premium delivers:
Policy enforcement
Browser governance
Context-aware security controls
Standardized configurations
Chrome Readiness Tool delivers:
Risk visibility
Exposure mapping
Migration readiness insights
Together, they create a practical lifecycle.
Session theft is not only a technical threat. It is a governance challenge that requires measurable visibility and consistent enforcement.
By combining insight with browser-level controls, organizations transform the browser from a potential vulnerability into a managed security boundary.

In today’s enterprise environment, security and cost efficiency must go hand in hand. Enterprises are increasingly discovering that the browser is no longer just a tool for productivity. It has become a critical perimeter for both risk and control. Chrome Enterprise Premium (CEP) and the Chrome Readiness Tool offer a combined solution that strengthens browser security while helping organizations optimize IT spending.
Security incidents in the browser carry significant financial implications. Data breaches, phishing attacks, and malware infections can result in costly remediation, downtime, and regulatory penalties. Traditional approaches to browser management often involve reactive measures, which increase IT overhead and inflate operational costs.
The Chrome Readiness Tool helps organizations identify vulnerabilities before they become problems. By mapping browser usage, surfacing unverified extensions, and highlighting unsecured domain access, the Chrome Readiness Tool allows IT teams to see exactly where risk exists. This visibility is crucial for making informed decisions about which devices, users, and workflows require security policies.
Chrome Enterprise Premium acts as a proactive layer of defense. With session-level Zero Trust controls, least-privilege enforcement, and phishing and malware protection, CEP prevents incidents rather than reacting to them. This reduces the financial burden of breach remediation and mitigates downtime that affects productivity.
By enforcing security policies consistently across all endpoints, CEP also reduces the need for manual IT intervention. This saves hours of support time that would otherwise be spent addressing security gaps or troubleshooting incidents. These operational efficiencies translate directly to cost savings.
When used together, the Chrome Readiness Tool and CEP create a strategic approach to browser security and IT spend.
Visibility first: The Chrome Readiness Tool provides a detailed view of browser readiness, application usage, and potential risk points.
Targeted action: IT can apply CEP policies only where they are needed, reducing overprovisioning and unnecessary license costs.
Proactive protection: CEP enforces security at the session level, preventing incidents that could incur significant expenses.
This combination ensures that organizations spend smarter rather than harder. Investments are applied in the right place at the right scale.
Enterprises see clear benefits from this approach.
Reduced incident response and remediation costs
Fewer support tickets and less IT labor spent on reactive fixes
Optimized license allocation for both users and devices
Faster, safer deployments of browser policies and applications
By aligning security measures with IT visibility, organizations can cut costs without compromising protection. This strategy empowers IT teams to focus on strategic initiatives instead of constant firefighting.
Cost efficiency and robust security are no longer separate objectives. With the Chrome Readiness Tool providing insight into browser readiness and CEP enforcing proactive security, enterprises can minimize risk while optimizing IT spend. Investing in visibility and control translates into measurable savings, a stronger security posture, and more efficient operations.
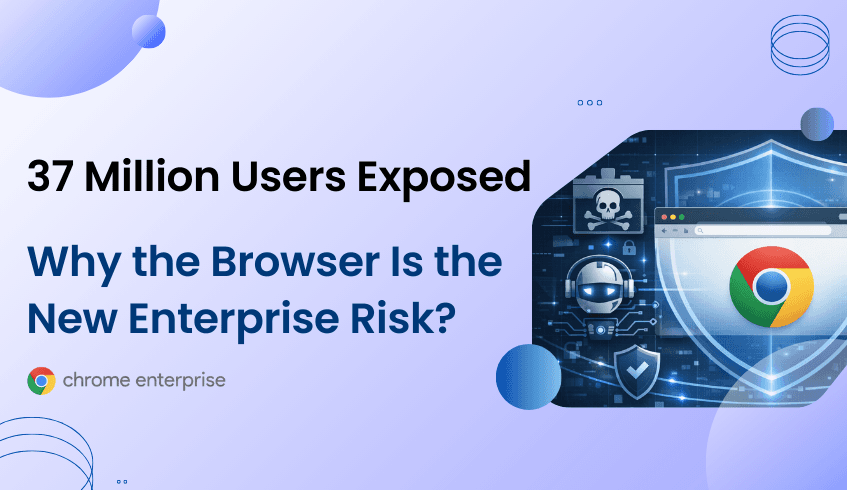
Over 300 malicious Google Chrome extensions have been discovered, affecting more than 37 million users globally. These extensions posed as AI assistants for summarization, writing, or Gmail integration but secretly extracted page content, accessed emails, and sent sensitive information to remote servers. Some campaigns even targeted social networks to take over accounts entirely.
This surge in browser-based attacks highlights a critical truth. The browser is now the primary attack surface. Perimeter defenses and traditional endpoint security are no longer enough for organizations. Malicious extensions bypass conventional protections, exploit user trust, and operate undetected.
These incidents reveal patterns enterprises cannot ignore.
Invisible Threats: Extensions embed remote-controlled interfaces that manipulate browser behavior without visible signs.
Credential Exposure: Some extensions target Gmail and corporate tools, increasing the risk of account compromise.
Evasion Techniques: “Extension spraying” publishes identical malicious code under different names to avoid takedowns.
Shadow Tools: AI-branded extensions appear legitimate, making risky usage hard to identify.
For IT leaders, the question is no longer if a malicious extension will appear but when. Understanding and controlling browser activity has become a business-critical priority.
Chrome Enterprise Premium enforces security directly where threats operate. By centralizing extension governance and applying policy controls, CEP reduces exposure before attacks occur. Key protections include
Extension Management: Approve trusted extensions and block high-risk installs
Behavior Controls: Prevent risky actions such as data exfiltration or unauthorized access
Data Protection: Apply browser-level DLP policies to safeguard emails, documents, and internal systems
Enterprise-wide Enforcement: Consistent policies across devices maintain compliance without slowing work
By governing browser behavior rather than reacting after compromise, organizations stop threats at their source while maintaining productivity.
Chrome Readiness Tool provides full visibility into real-world browser usage. IT teams gain insights into which pages employees access, identify shadow AI tools, and detect patterns that indicate risk.
Page-Level Visibility: Know which unsecured sites employees interact with
Shadow IT Discovery: Spot unauthorized or risky AI extensions
Exposure Mapping: Visualize browser usage trends to guide security strategy
Visibility empowers teams to act proactively. Together, CRT and CEP create a complete browser security framework: discovering risk, then controlling it.
The rise in malicious extensions is a warning. Threats can appear in trusted environments. Perimeter security alone is no longer sufficient. Enterprises need
Visibility to see where risk exists
Control to prevent threats from executing
Continuous evaluation to manage emerging tools and patterns
With Chrome Enterprise Premium for enforcement and the Chrome Readiness Tool for visibility, organizations reduce exposure to credential theft, data loss, and other browser-based attacks while keeping employees productive.
The browser does not have to be a blind spot. With the right tools, IT teams can see clearly, act decisively, and secure the environment where modern work happens.

Credentials are a critical part of enterprise security. Users log in to dozens of systems every day, from cloud applications to internal tools and legacy services. Weak password practices, reuse of corporate credentials, and credential theft are major risk factors that can lead to account compromise and data breaches. Chrome Enterprise Premium helps strengthen credential protection by preventing common risks and giving IT teams the visibility and controls they need to manage credential security across the browser environment.
Why Credential Protection Matters
Passwords serve as the primary authentication mechanism for most enterprise resources. When these credentials are reused, compromised, or entered into unsafe web pages, attackers can gain unauthorized access to sensitive systems. Phishing attacks, malicious websites, and credential stuffing campaigns all target weaknesses in how users handle credentials. Preventing reuse of corporate passwords and blocking unsafe credential practices reduces the likelihood that attackers succeed at gaining a foothold in enterprise systems.
Chrome Enterprise Premium includes password protections that help IT teams manage these risks at scale. This capability goes beyond basic browser password management by helping to prevent corporate password reuse and providing reporting so administrators can see where risky practices occur. While basic browsing includes standard protections, the Premium tier adds reporting and enforcement that give organizations actionable insights into credential health.
Integrating Visibility with Credential Practices
Before applying strong credential protections, IT teams need to understand how credentials are being used throughout the organization. The Chrome Readiness Tool’s Browser Insights complements Chrome Enterprise Premium by revealing patterns in browser usage. Browser Insights can show where risky domains are accessed and how often users encounter unsafe sites.
By analyzing this readiness data, security teams can identify high‑risk areas and user groups that would benefit most from targeted credential protections. Visibility into credential exposure before policy deployment helps avoid blanket controls that could disrupt productivity and instead allows policies to be tailored to the organization’s real risk profile.
Deploying Credential Protections at Scale
Once risky credential practices are understood, Chrome Enterprise Premium allows IT teams to implement protections across the enterprise fleet. Administrators can apply policies that prevent employees from reusing corporate passwords on unsafe websites, monitor for credential reuse events, and receive reporting that highlights where additional training or policy refinement is needed.
Because these protections are natively integrated into the browser, they apply consistently across devices and operating systems without requiring endpoint agents. Centralized management of browser security policies lets security teams enforce credential protections across both managed and unmanaged devices without slowing down the user experience.
Chrome Enterprise Premium also includes other security controls that support credential protection efforts. Real‑time phishing and malware protections warn users before they enter credentials on harmful sites. Context‑aware access controls can restrict access to sensitive resources unless additional conditions such as device security posture, are met. These layered protections make it harder for attackers to collect credentials through deceptive or malicious channels.
Measuring Impact and Refining Strategy
Credential protection is not a one‑time task. As threats evolve and user behavior changes, IT teams must monitor how credential protections are working and adapt where needed. Chrome Enterprise Premium’s reporting and analytics help track credential reuse attempts, unsafe sign‑in events, and user interactions with high‑risk sites. These insights help security teams refine policies and craft user education programs that promote safer password practices.
Turning Browser Security Into Credential Confidence
By combining Chrome Enterprise Premium’s credential protections with the visibility that Chrome Readiness Tool Browser Insights provides, organizations gain a comprehensive approach to credential security. Teams can spot risky practices, act with precise policies, and track outcomes over time. This integrated approach reduces exposure to credential theft and misuse while maintaining the productivity and flexibility users expect from modern web browsing. As enterprises continue to evolve their security postures, browser‑native protections provide an essential layer of defense for credential integrity.
Managing browser security and performance across a large enterprise is a complex challenge. Hundreds or thousands of devices need monitoring, policies must be applied consistently, and IT teams must balance protection with employee productivity. Chrome Enterprise Premium addresses this by embedding advanced security and analytics directly into the browser, giving IT teams centralized control without disrupting workflows.
Centralized Visibility Into Enterprise Browser Health
With Browser Security Analytics, Chrome Enterprise Premium provides a clear view of enterprise browser health. IT teams can see which devices are secure, moderately secure, or not secure, and monitor organization-wide risk metrics such as session theft incidents, unverified extensions, and unsecured domain access. This data allows IT leaders to prioritize remediation for high-risk devices, enforce policies strategically, and reduce exposure to threats before they escalate.
Understanding Usage and Targeted Enforcement
The Chrome Readiness Tool Browser Insights complements this by showing how browsers are used across the organization. It identifies unsafe extension usage, unsecured domain access patterns, and inconsistent device configurations. Linking these findings with Chrome Enterprise Premium analytics enables IT teams to plan targeted policy deployments, guide user training, and monitor the effectiveness of security measures over time. This ensures that both security and productivity goals are met.
Browser Insights also accelerates migration and scaling of Chrome Enterprise Premium across large fleets. IT teams can prioritize devices or user groups that need immediate attention, addressing critical gaps early. This helps maintain consistent policy application and reduces the likelihood of security incidents during deployment.
Continuously Optimizing Security and Performance
Combining Chrome Enterprise Premium with Chrome Readiness Tool Browser Insights allows organizations to continuously optimize browser performance. Trends in device security, extension usage, and unsecured domain access provide actionable intelligence for policy adjustments, hardware upgrades, and proactive user guidance. This data-driven approach keeps browsers secure and performant even as enterprise needs evolve.
Managing the Browser as a Secure Enterprise Platform
Enterprises that pair Chrome Enterprise Premium with Chrome Readiness Tool Browser Insights gain the visibility, enforcement, and intelligence needed to manage browser security at scale. Organizations can confidently reduce risk, maintain consistent performance, and create a secure environment for employees to work efficiently across devices and applications. The browser becomes more than a tool; it becomes a managed platform for secure, productive enterprise work.

As generative AI tools and collaboration platforms grow, sensitive data increasingly moves through the browser. Employees routinely copy, paste, and upload information between applications as part of normal work. Without browser-level controls, these actions can create exposure that traditional security tools often miss. Chrome Enterprise Premium brings data protection directly into the browser workspace.
Mitigating Risk in Everyday Actions
Most data leaks do not start with malicious intent. Tasks such as pasting content into AI tools or uploading files to external services can cross compliance boundaries. When monitoring stops at the network or application level, these movements often go ungoverned. Chrome Enterprise Premium applies Data Loss Prevention policies inside live browser sessions. Sensitive content can be blocked from being copied into unauthorized platforms, uploaded externally, or printed without approval. Controls are enforced at the moment data is handled, preventing exposure before it happens.
Visibility and Targeted Enforcement
The Chrome Readiness Tool provides visibility into how data moves across the organization. It highlights unsanctioned AI usage, unsecured upload destinations, and high-frequency data transfer patterns. These insights reveal where copy-paste and upload risks are most likely to appear. By aligning these insights with browser enforcement, IT teams can apply controls precisely. High-risk users, devices, or workflows can be addressed first, while low-risk activity continues uninterrupted.
Learning and Adapting Over Time
DLP activity becomes a valuable signal for policy refinement. Repeated attempts to share sensitive data or consistent use of unapproved tools indicate where policies should be updated or user guidance strengthened. Security teams gain the ability to adapt controls as browser behavior evolves, turning previously invisible data movements into actionable intelligence.
From Data Blind Spots to Confident Control
Together, Chrome Enterprise Premium and the Chrome Readiness Tool turn data movement inside the browser into a manageable layer of protection. Organizations can reduce copy-paste leaks, safeguard sensitive information, and maintain the pace of modern work without disruption.

Attackers Are Targeting Active Sessions
As organizations strengthen identity and access management, attackers are shifting their focus to browser sessions. Once a user logs in, session cookies effectively become keys to corporate systems. If stolen, they allow access without triggering password or MFA checks. This makes session security one of the most critical and often overlooked layers of enterprise protection. Chrome Enterprise Premium secures sessions at the point where work actually happens.
Security Must Extend Beyond Login
Relying only on authentication is no longer sufficient. Modern security strategies must evaluate activity after access is granted. Browser sessions capture live interactions with SaaS platforms, internal tools, and sensitive workflows. Protecting this layer keeps verified identities protected throughout active use, not just at the moment of entry.
Context-Aware Controls Inside the Browser
Chrome Enterprise Premium brings continuous, context-aware access controls directly into the browser. These controls assess device posture, user identity, and access context in real time. If a session cookie is reused from an untrusted device or a suspicious location, access can be restricted immediately. This stops attackers from abusing stolen sessions even when credentials appear legitimate.
Identifying Where Session Risk Lives
The Chrome Readiness Tool strengthens this approach by revealing where session-related risks are most likely to emerge. It surfaces unmanaged devices, insecure access patterns, and high-risk browsing behaviors that increase exposure. These insights help IT teams focus protections before incidents occur.
Precision Instead of Blanket Restrictions
By combining readiness insights with browser-native enforcement, organizations can apply controls with precision. Instead of broad restrictions that impact everyone, protections can be targeted to high-risk users, devices, and workflows. This approach improves security while supporting productivity.
Turning Session Activity Into Security Signals
Over time, session-based incidents become valuable intelligence. Security teams can analyze patterns such as repeated access from unknown devices or inconsistent location behavior. These signals support smarter policy refinement and stronger identity protection strategies.
From Reactive Defense to Proactive Control
With Chrome Enterprise Premium and the Chrome Readiness Tool working together, session security evolves from a reactive concern into a proactive control layer. Enterprises gain continuous protection across every browser interaction, closing gaps that traditional identity defenses no longer cover.